Choosing a remote identity verification solution for a KYC process involves several factors: security, regulatory compliance, user experience and, last but not least, speed. Making the right choice is crucial to ensuring a high conversion rate while protecting your users.
Criteria for choosing a KYC solution
Your needs
Above all “technical” criteria, it’s important to choose a remote identity verification solution based on your needs. For example, a bank looking to obtain an identity verification solution for remote underwriting, or to set up its KYC remediation campaign, will not have the same criteria as a start-up or SME such as a small business school that simply wants to automate the enrolment process for new students. The choice depends on your business sector and your needs.
Safety
It is essential to ensure that the solution is robust in terms of personal data protection and fraud prevention. Here are a few things to consider:
- Data encryption: Check whether the tool uses robust encryption to guarantee the confidentiality of personal data. Ideally, the solution should use military-grade encryption, such as AES-256.
- Server security: Ensure that servers are protected by firewalls and that intrusion detection mechanisms are in place to prevent attacks.
- Anti-fraud: Find out more about the anti-fraud features integrated into your solution. Tools such as false document detection, document integrity verification and information consistency analysis can help prevent fraud attempts. To combat fraud, solutions such as the Qualified Electronic Signature of the eIDAS regulation are often envisaged.
Find out more by downloading our free replay of the Webinar entitled “Webinars & Replays”.Remote identity verification & AI: between myth and reality”
Webinar
Compliance with current regulations
Anti-money laundering and combating the financing of terrorism (LCB-FT) regulations require companies in certain sectors such as banking and insurance to comply with KYC procedure to verify the identity of their customers and the validity of the identification documents provided. The most stringent regulations require the use of solutions such as Netheos ID MAX, PVID certified by ANSSI, or Netheos ID FAST for Qualified Electronic Signature (QES), eIDAS certified.
Make sure it incorporates the most advanced features, such as Optical Character Recognition (OCR ) for automatic document reading, and Machine Learning facial recognition.
In addition, check whether the solution offers real-time checking of sanctions lists and international databases, to ensure that your customers are not involved in illegal or terrorist activities.
Finally, make sure that your identity verification solution respects the confidentiality and security of your customers’ personal data. As such, it must comply with the General Data Protection Regulation (GDPR) and use secure encryption protocols for data storage and transmission.
User experience (UX)
User experience is a key criterion to consider when making your selection, as it will determine how easy the solution is to use for your end-users. An intuitive, user-friendly solution will guarantee a smooth, pleasant experience, contributing to customer satisfaction and higher conversion rates.
When evaluating a solution, make sure it offers a clear, well-designed user interface. Verification steps should be simple to follow, with clear, understandable instructions. Avoid complex interfaces and too many steps, which can discourage your users and compromise conversion.
The user-friendliness of the solution is also a key factor. Make sure the interface is adapted to different types of device (computers, smartphones, tablets) and optimized for mobile use.
Last but not least, don’t forget to take into account additional functionalities that can enhance the user experience. For example, a solution that offers real-time identity verification, with the option of taking photos or submitting documents directly via the application, will be more convenient for your users… The most advanced solutions, such as Netheos ID FAST, enable you to perform the live video identity verification and passive live detection, saving users a considerable amount of time.
Speed
To assess the speed of a KYC solution, you need to check whether it offers live verification or requires a processing time. Real-time verification saves you valuable time, which is essential for ensuring a smooth, seamless experience for your users. Netheos solutions are the fastest and smoothest on the market: Netheos ID FAST and its ®Facematch Video allow a completion time of less than 40 seconds, maximizing your conversion rates!

Make an appointment with one of our experts to find out how Netheos solutions can help you verify the identity of your users, securely and without loss of conversion.
Netheos remote identity verification solutions
Secure identity verification with ®Facematch
All our KYC solutions incorporate our proprietary ®Facematch facial recognition technology. It adds an extra level of security to remote identity verification. Netheos ®Facematch is :
- A Machine Learning algorithm to protect against identity theft by ensuring that the person making the journey corresponds to the owner of the identity document.
- Simple operation via a camera integrated into a smartphone, tablet or computer
- 3 formats to suit your compliance and security needs: ®Facematch Photo, ®Facematch Video and ®Facematch MAX

3 KYC solutions tailored to your needs
Netheos ID+
The historic solution most used by our customers. Our ®Facematch Photo facial recognition technology eliminates the risk of identity theft. The fully guided tour offers a very high conversion rate, with an average completion time of 48 seconds.
Use: Simple KYC process for customer onboarding, with little need for compliance
LCB-FT compliance: If combined with a SEPAm@il diamond solution
-
Capture identity document
Users take photos of their documents with their smartphone, or download them if they have previously captured or scanned them.
-
Document quality control
The user checks that the quality of the document conforms to specifications (sharpness and completeness). He can start again if necessary.

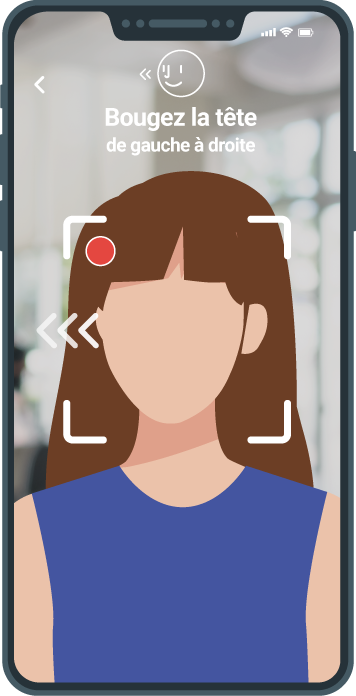
-
Active facial recognition
The user needs to make brief movements to guarantee his presence and liveliness. This step ensures that the user is the legitimate holder of the identity document.
-
Sent for analysis
Final verification is carried out according to 3 different levels of automation: 100% automatic (based on AI controls), hybrid (configurable human intervention) or 100% manual.
Netheos ID FAST
The Video version of our ®Facematch facial recognition technology not only eliminates the risk of fraud, but also simplifies the entire user experience: the conversion rate is maximized with a completion time of less than 40 seconds, offering the best user experience on the market.
Use: Qualified Electronic Signature (QES), smooth customer onboarding KYC process
LCB-FT compliance: if used for Qualified Electronic Signature (QES)
-
Video capture of identity document
Capture is live: the user frames his document, which he must have in his possession.
-
Passive facial recognition
At this stage, live detection is passive and transparent for the user: no action is required. This step ensures that the user is the legitimate holder of the identity document.
-
Sent for analysis
Final verification is carried out according to 3 different levels of automation: 100% automatic (based on AI controls), hybrid (configurable human intervention) or 100% manual.
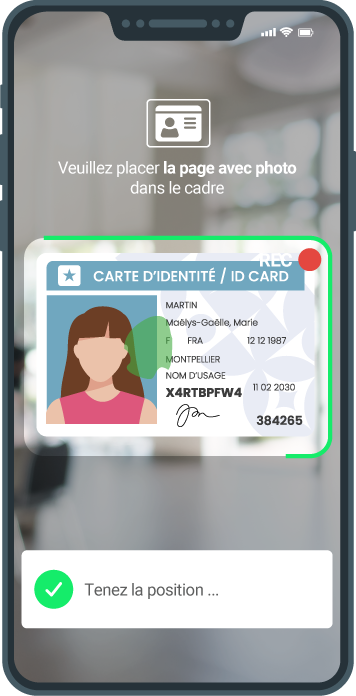
Netheos ID MAX
Remote identity verification pathway currently undergoing PVID certification by ANSSI to meet legal obligations imposed on certain sectors. The Netheos PVID pathwaycombines AI and human experts, available 24/7 and based in France, with an end-to-end pathway in less than 2 minutes.
Usage: PVID course
LCB-FT compliance: Solution audited and in the process of being certified by ANSSI, 100% LCB-FT compliant.
-
Video capture of identity document
Capture is live: the user frames his document, which he must have in his possession.
-
Checking the authenticity of identity documents
Manipulations are required to verify that the title is authentic by detecting embossing, inks and holographic visual effects.
-
Passive facial recognition
At this stage, live detection is passive and transparent for the user: no action is required. This step ensures that the user is the legitimate holder of the identity document.


-
Active facial recognition
To reinforce identity control, active liveliness detection is required: the user must speak 3 random digits, which appear on the screen.
-
Sent for analysis
The final verification is carried out by a human operator who, with the help of Artificial Intelligence, checks the authenticity of documents and videos. At Netheos, this service is staffed by anti-fraud experts based in France and available 24/7. We guarantee a final result in less than 5 minutes.
- KYC for banks: role and impact in 2023
- Customer onboarding: definition and operation
- What is KYC in crypto?
- What is Regtech?
- Artificial intelligence: impact on KYC in 2023
Fill in the form and we will contact you as soon as possible.
You can discover :
- How we can meet your specific needs and expectations
- A personalized demo, allowing you to appreciate the fluid experience we offer
- Customer feedback and case studies of similar companies that have integrated our solutions
- Advantages, benefits and value according to your use case
